What is a Crypto Dust Attack and How Do I Avoid It?

Have you ever observed an insignificant amount of cryptocurrency in your digital wallet that you could not recall receiving?
Initially, you might have been exhilarated, presuming that someone had accidentally transferred funds to you.
However, the truth is that you may have become the victim of a Crypto Dust Attack, and if you fail to take necessary precautions, you may lose money.
This article will shed light on the intricacies of crypto dusting attacks, delineate the parties that may be vulnerable to such an attack, and suggest measures to mitigate such malicious activities.
What is Crypto Dust?
In order to send crypto you have to pay a network fee. The size of this fee usually depends on the current level of network congestion. For example, Bitcoin at its peak required paying more than $60 per transaction while PoS-based cryptocurrencies like Solana or TRON usually demand less than a cent.
BitInfoCharts: in April 2021, the Bitcoin network fee reached ~$62.8
Regardless of the network, the fees hardly ever represent a rounded number. Thus, when you send all your crypto to someone else, you will usually find some small leftovers in your wallet. This is exactly what the term dust refers to.
This phenomenon is possible thanks to crypto divisibility, one of the key technical aspects that make cryptocurrencies stand apart from traditional fiat money. It means that cryptocurrencies can divide into much smaller units than US dollars or other traditional money. For example, the smallest Bitcoin unit satoshi equals 0.00000001 BTC.

While this feature can be useful for micro-transactions, it may be used to compromise crypto wallet security.
What is a Crypto Dust Attack?
A crypto dust attack is a tactic used by hackers or spammers to compromise the privacy and security of cryptocurrency users. It involves sending tiny amounts of cryptocurrency (referred to as "dust") to a large number of crypto wallets in order to track and potentially link the addresses together.
The dust is usually sent in a way that is difficult for the user to notice, often as small amounts of a few satoshis (the smallest unit of Bitcoin). Once the dust is received, it can be used to track the recipient's activity on the blockchain, potentially revealing personal information and transaction history.
In addition to tracking, dust attacks can also be used to spam users with unwanted transactions or to clog up the network with small, useless transactions. These attacks are often carried out using automated scripts or bots, making them relatively easy and cheap to execute.
If you have ever received one or many small incoming crypto payments to your wallet, you may have been dusted. While the dust itself doesn’t bear any harm, it may help attackers if you start moving it around.
Typically, crypto dust attacks pursue different goals depending on the asset type.
1. Account-based assets
Such an approach to storing crypto implies managing your digital assets in a way similar to a traditional bank account. Simply put, this is your basic account where you store all your coins such as BTC, ETH, TRX, or any other crypto.
When attackers send dust to such accounts, they may include malicious links in the transaction description. These links may lead to phishing websites or malware or prompt you to share your personal data.
2. UTXO-based assets
Unspent transaction output, or shortly UTXO, represents the remnants of crypto that you have in your wallet after you have completed an outgoing transaction. This part of crypto is stored separately from the overall account balance.
Attackers may send crypto dust to such addresses and analyze subsequent crypto moves. Thus, they can reveal the identity of the wallet owner.
What Does Crypto Dust Attack Look Like?
Crypto dusting is a small amount of crypto that comes from an unknown address. It may be a single transaction or it may be a series of transactions performed within a period of time.
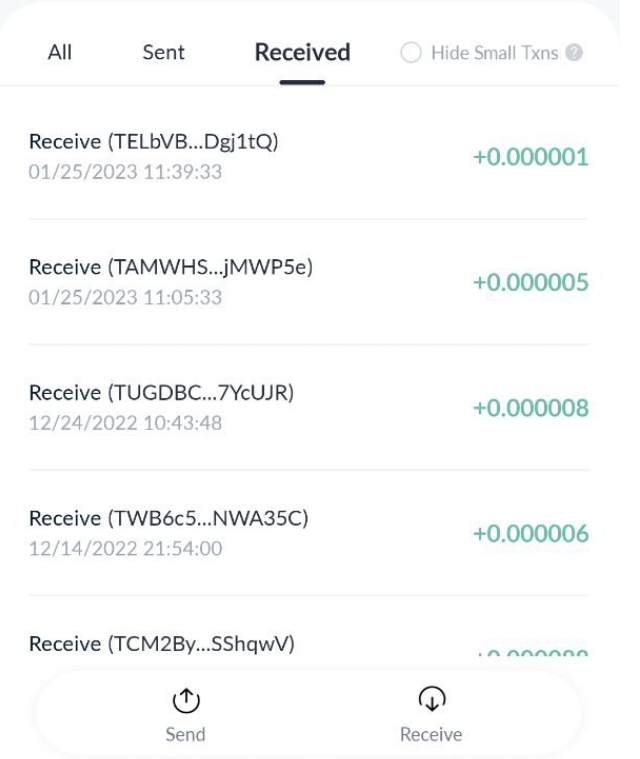
A crypto dust attack in a TronLink wallet
How Does a Crypto Dust Attack Work?
Crypto dusting usually implies sending small amounts of crypto to multiple addresses without targeting anyone specifically.
The crypto dust that you may receive in your wallet doesn’t bear any harm by itself. This is just a small fraction of crypto hardly sufficient even to cover transaction fees. Yet, if you combine it with a solid sum of other digital assets to send them somewhere else, you may put your wallet at risk.
Blockchain provides full transparency into users’ wallets and their balances. Attackers analyze all addresses that have received crypto dust and link all the traces that they leave in the network. Thus, they can identify different wallets that belong to the same person.
Who Performs Crypto Dusting Attacks?

Crypto dust transactions require network fees, just like any other transaction on the blockchain. At this, sending dust to thousands of addresses may cost a fortune, especially when an attacker performs dusting on Bitcoin or other expensive networks.
Who would go to such extremes? Essentially, there are a few key groups.
1. Criminals
Malicious actors may use crypto dusting while looking for a big fish in the ocean of smaller targets.
Crypto dust attacks may help such criminals identify large crypto holders in the list of regular crypto users. Having revealed potential victims, criminals may elaborate phishing attacks or perform other malicious activities aiming to steal digital assets.
Alternatively, a large criminal gang may try to hide its own traces. In this case, crypto dust acts as a smoke screen helping criminals to spread the dirty money and throw the watchdogs off the trail.
2. Authorities
Governmental financial structures may use crypto dusting to identify people or a group of people linked to a specific address. Thus, they may reveal large criminal networks, gangs, tax evaders, or those engaged in money laundering.
3. Analytical companies
Such companies perform crypto dusting as they pursue academic goals while studying various aspects of blockchain networks.
Interestingly, you don’t have to conduct a crypto dust attack yourself in order to use the information it reveals.
Imagine there has been a crypto dusting attack that gained some traction in the large media. Governments as well as analytical companies may identify the scope of this attack and use the information for their own purposes without spending any money.
4. Blockchain companies
The companies may use mass crypto dust as a stress test for their own networks. Thus, crypto dusting helps them to test the throughput indices. Alternatively, they may attack their competitors aiming to spam their networks and slow them down.
In addition, crypto companies may send out crypto dust in a form of free airdrops. Such airdrops may even bear real value. The goal of such an attack is to get users interested and to reveal themselves by moving these tokens across exchanges.
How to Counter Crypto Dust Attacks?
Protecting yourself from crypto dusting is not rocket science. With a diligent approach to the security of your digital assets, there’s nothing you should fear.
Here are some tips that can help secure your funds in case you received crypto dust:
1. Ignore dust transactions.
It may seem to be too easy, but in fact, it’s the best way to protect your wallet on such occasions. As mentioned earlier, the dust itself doesn’t bear any harm. So if you leave it in your wallet as is, you won’t give out any information about yourself to attackers and thus leave them empty-handed.
2. Use hierarchical-deterministic (HD) wallets.
Such wallets generate new keys for every transaction. This helps to improve your privacy and security making it more complicated for attackers to trace you.
In addition, there are wallets that enable their users to mark UTXOs so as to totally block their usage. Thus, they prevent spending crypto dust in an absent-minded manner.
3. Isolate the dust on a separate wallet.
Multiple incoming dust transactions can mix up with your other addresses. Unwary users may convert dust into other assets or use it when sending their funds elsewhere and thus reveal their identities to attackers.
Storing the incoming dust on an isolated account may give you better protection.
4. Follow general security practices
Do not download suspicious files and do not click on unknown links.
Do not interact with unverified tokens unless you are 100% sure of the source they came from.
Do not share any personal information that may help malicious actors connect your identity with your wallet.
Bottom Line
For the majority of crypto users, dust attacks do not represent any real harm. Unless you store a really large sum in crypto or live in a politically unstable region, there is nothing you should fear of.
Crypto dust doesn’t expose your private keys to anyone. Neither does it provide any external party with your personal information. Leave it untouched, and you won't suffer any questions.
Join The Leading Crypto Channel
JOINDisclaimer:Please note that nothing on this website constitutes financial advice. Whilst every effort has been made to ensure that the information provided on this website is accurate, individuals must not rely on this information to make a financial or investment decision. Before making any decision, we strongly recommend you consult a qualified professional who should take into account your specific investment objectives, financial situation and individual needs.

Kate
Kate is a blockchain specialist, enthusiast, and adopter, who loves writing about complex technologies and explaining them in simple words. Kate features regularly for Liquid Loans, plus Cointelegraph, Nomics, Cryptopay, ByBit and more.

Development
Knowledge
Subscribe To Newsletter
Stay up-to-date with all the latest news about
Liquid Loans, Fetch Oracle and more.
Copyright © 2024 Crave Management.
All Rights Reserved.

The LL Librarian
Your Genius Liquid Loans Knowledge Assistant